The unassuming click of a “Pay Now” button initiates a complex dance of data, security, and financial institutions. For the end-user, it’s seamless; for us, the architects and engineers behind the scenes, it’s a testament to robust distributed systems. This blog post isn’t about integrating existing APIs; it’s about peeling back the layers and understanding the fundamental components, challenges, and best practices involved in building a payment gateway solution from the ground up. We’ll delve into the minutiae of protocols, advanced security, resilient architectural patterns, and crucial operational considerations that define success in this mission-critical domain.
1. The Payment Gateway: More Than Just a Middleman
Beyond a simple conduit, a payment gateway functions as a sophisticated, high-throughput, low-latency financial transaction orchestrator. It sits at the nexus of trust, securely mediating complex interactions between merchants and the vast financial ecosystem.
Key Functions:
- Secure Cardholder Data (CHD) Ingestion & Handling: This involves meticulous handling of sensitive payment information. It’s not just basic encryption, but adherence to point-to-point encryption (P2PE) standards from the payment terminal or browser to the gateway’s secure environment, minimizing the attack surface. Crucially, tokenization must be implemented at the earliest possible stage, replacing CHD with a non-sensitive token. For detailed requirements, refer to the official PCI DSS P2PE Solution Requirements.
- Transaction Protocol Translation: The gateway translates merchant-friendly API calls into standardized financial messaging formats. The most prominent is ISO 8583, an international standard for financial transaction card originated messages. This involves intricate field mapping, data packing, and unpacking specific to various payment networks (e.g., VisaNet Base II, Mastercard IPS). The ISO 8583 standard is the foundational document for these interactions.
- Dynamic Transaction Routing: Advanced routing logic is vital for optimizing performance, cost, and resilience. Parameters include card BIN (Bank Identification Number) for optimal processor selection, merchant risk profile, transaction amount, currency, geographic region, real-time processor uptime/latency, and even cost optimization models based on interchange rates.
- Lifecycle Management (Authorization, Capture, Void, Refund):The gateway must maintain a comprehensive, consistent state for each transaction throughout its lifecycle. This often involves an eventual consistency model across distributed systems, with mechanisms for compensating transactions in case of partial failures.
- Advanced Risk & Fraud Analytics: Implementing robust fraud detection involves integrating real-time behavioral analytics, device fingerprinting, machine learning inference engines, and consortium data alongside traditional rule-based systems. This proactive, multi-layered approach is critical for reducing financial losses due to fraud.
- PCI DSS & Regulatory Compliance: Beyond mere adherence, this demands proactive architectural design to reduce PCI scope (e.g., achieving SAQ A-EP or SAQ P2PE for merchants), attaining PCI DSS Level 1 Service Provider certification, and adapting to evolving regulatory landscapes (e.g., PSD2’s Strong Customer Authentication (SCA) in Europe, GDPR for data privacy, CCPA in California, and local data residency laws). Comprehensive guidance is available from the PCI Security Standards Council.
- Reconciliation & Reporting Microservices: Generating detailed audit trails, settlement reports (often in specific formats like OFX, MT940), and providing analytical insights for merchants and internal operations are essential. Accuracy and timeliness of these financial reports are paramount.
2. The Ecosystem Unveiled: Key Players in a Transaction Flow
Understanding the interaction model is crucial. The payment gateway abstracts much of this complexity for the merchant, acting as the central orchestrator.
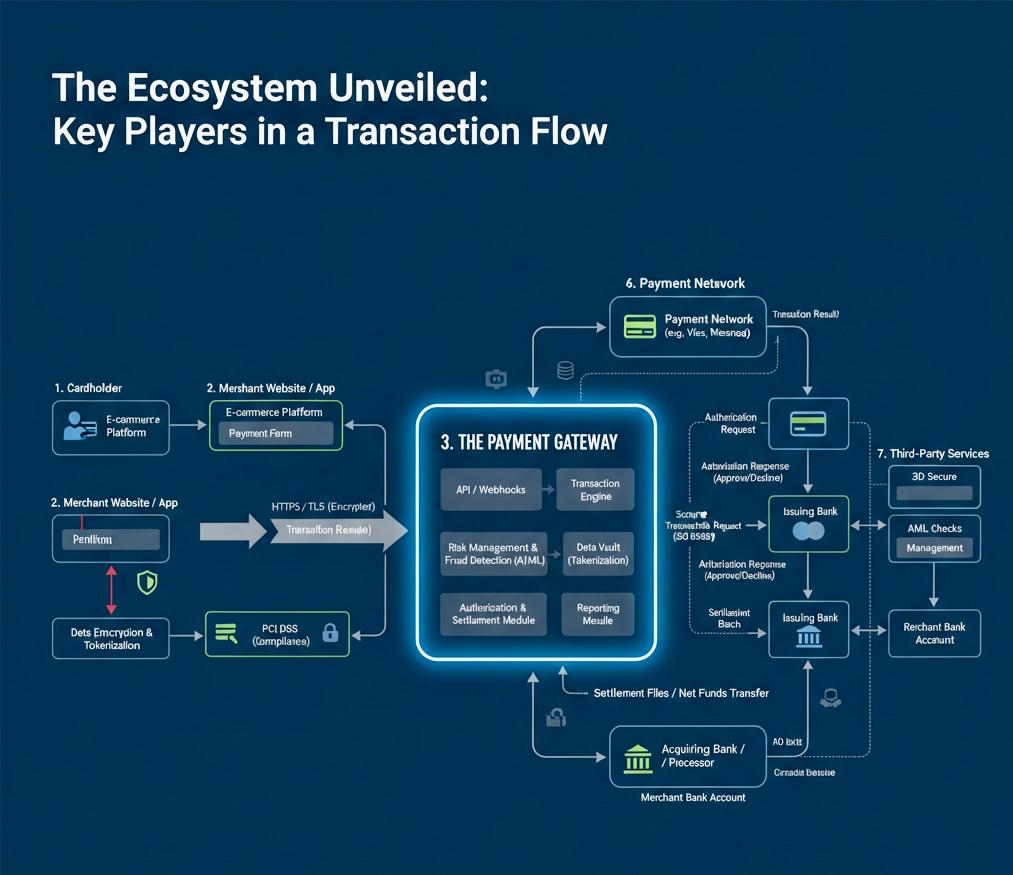
- Cardholder: This is the customer who initiates the payment, providing their sensitive cardholder data (CHD) typically through an e-commerce platform.
- Merchant Website/App: The business or e-commerce platform that sells goods or services. Their PCI DSS (Payment Card Industry Data Security Standard) compliance scope is significantly influenced by how they integrate with the payment gateway—for example, using hosted fields or iframes (which reduces their scope) versus handling raw card data directly. All communication involving CHD is secured via HTTPS/TLS.
- The Payment Gateway: Our core system. It acts as the secure intermediary, performing critical functions such as card data tokenization, encryption, sophisticated fraud checks (AI/ML), dynamic transaction routing to optimal processors, protocol translation, and managing the overall state of the transaction. Key internal modules include:
- API/Webhooks: The primary interface for merchants.
- Transaction Engine: Orchestrates the core transaction flow.
- Risk Management & Detection (AI/ML): Evaluates transactions for fraud.
- Data Vault (Tokenization): Securely stores token-to-PAN mappings.
- Dynamic Routing: Directs transactions to the appropriate acquiring bank/processor.
- Authorization & Settlement Module: Handles approval/decline logic and prepares for fund transfers.
- Reporting Module: Generates transaction reports.
- Acquiring Bank/Processor: This financial institution processes credit and debit card transactions on behalf of the merchant. It acts as the merchant’s bank in the transaction chain, receiving settlement funds. Transaction communication (e.g., authorization requests/responses) often leverages standardized ISO 8583messages. They may also perform their own AML checks.
- Payment Network/Card Schemes (e.g., VisaNet, Mastercard’s IPS): These are the global, highly secure communication networks (like Visa and Mastercard) that connect acquiring banks with issuing banks. They establish the messaging standards (e.g., specific ISO 8583 message types for authorization requests, advices, and responses) and govern the rules for interchange fees.
- Issuing Bank: The cardholder’s bank, which issued the credit or debit card. It’s responsible for approving or declining transactions based on factors like available funds, credit limits, and its own fraud detection mechanisms. It also plays a role in 3D Secure authentication.
- Third-Party Services:
- AML Checks: Anti-Money Laundering services for verifying identities and monitoring suspicious activity.
- Fraud Check/Approve/Decline: Additional fraud scoring and decisioning tools.
- Reconciliation: Services to assist with matching transactions and settlements.
3. Architectural Blueprint: Deconstructing the Gateway
A modern payment gateway leverages a microservices architecture, event-driven patterns, and robust distributed system principles to achieve its stringent requirements.
- Monolithic vs. Microservices (Comparative Analysis):
While a monolithic architecture might offer simpler initial deployment and management, its tight coupling quickly becomes a severe bottleneck for scalability, independent feature deployment, and fault isolation in a high-transaction, high-security environment. A single failure can bring down the entire system, and scaling one component means scaling all.
Conversely, a microservices architecture allows for specialized teams, independent technology choices per service, and granular scaling of individual components (e.g., scaling the FraudServiceindependently of the ReportingService). This provides superior resilience and agility. The trade-off lies in increased operational complexity, the need for robust distributed transaction management (often with eventual consistency and compensation), and sophisticated observability. Given the demands of payment processing, most modern gateways overwhelmingly opt for microservices to meet performance, security, and agility requirements. - API Gateway & Edge Services Layer:
This is the ingress point for all merchant requests.- Authentication & Authorization: Implemented with secure mechanisms like JWTs, OAuth 2.0 (specifically the Client Credentials Grant for server-to-server communication), and a robust API key management system with granular permissions.
- Rate Limiting & Throttling: Crucial for protecting downstream services from abuse, accidental overload, or unexpected traffic spikes. Distributed rate limiting solutions (e.g., using Redis or specialized proxies like Envoy with rate limit filters) are employed.
- Input Validation & Schema Enforcement: Ensures only well-formed and valid requests proceed, often leveraging OpenAPI/Swagger for strict contract definition and automatic validation.
- Security: This layer integrates Web Application Firewalls (WAFs), Distributed Denial of Service (DDoS) protection, and manages TLS termination to secure communication.
- API Versioning: Careful management of backward compatibility for merchant integrations using strategies like URL-based (/v1/), header-based, or content negotiation.
- Transaction Processing Engine (Core Logic):
This is the intelligent heart orchestrating the transaction.- Orchestration Engine: A state machine-driven service responsible for coordinating calls to various microservices (e.g., FraudService, TokenizationService, NetworkAdapterService). Modern workflow engines (e.g., Cadence, Temporal) are often employed to manage complex, long-running transaction lifecycles, enabling visibility, retries, and compensation for multi-step processes across distributed services.
- Network Adapter Services: Dedicated microservices, each specialized to communicate with a specific acquiring bank/processor or payment network. Each adapter understands the nuances of its particular endpoint (e.g., variant ISO 8583 implementations, proprietary API structures, unique connection pooling, message sequencing requirements, specific header/trailer formats). This isolation prevents a change in one processor’s API from impacting others.
- Idempotency Service: A centralized service leveraging distributed locks (e.g., Redlock with Redis) or unique transaction IDs to ensure that an operation produces the same result regardless of how many times it’s executed. This is critical in distributed systems prone to retries and network issues, preventing duplicate charges.
- Security & Compliance Module (Fortress Design):
The most sensitive part of the gateway, engineered for maximum protection.- Hardware Security Modules (HSMs): Essential for cryptographic operations (key generation, encryption/decryption, digital signatures) and secure storage of master keys. HSMs provide FIPS 140-2 Level 3 (or higher)compliance, offering tamper-evident physical security and robust key management.
- Tokenization Service: Generates format-preserving tokens (FPT) or non-format-preserving tokens (NFPT). It securely stores the token-to-PAN (Primary Account Number) mappings in a highly secure, segregated data store known as the “token vault.” Best practices for tokenization are detailed in PCI DSS Tokenization Guidelines.
- Key Management System (KMS): Securely manages the lifecycle of all encryption keys – generation, rotation, revocation, access control. Often integrates directly with HSMs for the root of trust.
- Vault Architecture: A physically and logically isolated environment for Cardholder Data (CHD). Typically comprising a separate network segment, dedicated hardware or highly isolated cloud resources, stringent access controls, and comprehensive auditing. This segregation is a cornerstone of PCI DSS compliance.
- Risk Management & Fraud Detection Engine (Intelligence Layer):
A highly dynamic and intelligent system for real-time threat analysis.- Data Pipelines: Real-time ingestion and processing of transactional data, device data, IP intelligence, and historical fraud data into a stream processing system (e.g., Kafka Streams, Flink).
- Feature Engineering: Deriving high-value features for machine learning models (e.g., velocity of transactions from a single IP, card BIN country vs. shipping country, chargeback history of the merchant/cardholder).
- ML Inference Service: Deploys trained models (e.g., XGBoost, Neural Networks) to provide real-time risk scores for each transaction. This can trigger dynamic actions like challenging via 3D Secure or an immediate hard decline.
- Rules Engine: A customizable system (e.g., Drools, custom DSL) for implementing business rules and thresholds based on risk scores and other attributes. Provides flexibility for fraud analysts to adapt to new patterns without requiring code deployments.
- Chargeback Management: Automated systems to track, dispute, and manage chargebacks. This often integrates with case management tools, reducing manual effort and improving recovery rates.
- Data Persistence Layer:
A varied landscape of databases optimized for different workloads.- Transaction Log Database: A high-throughput, write-optimized database (e.g., Cassandra, DynamoDB, sharded PostgreSQL) for immutable transaction records. Event sourcing patterns are often applied here for a complete, verifiable audit trail.
- Operational Database: Relational databases (e.g., PostgreSQL, MySQL) for merchant configurations, user data, and other referential integrity needs.
- Token Vault: A highly specialized, encrypted data store, often a separate instance or cluster, specifically for storing the token-to-PAN mapping with extremely strict access controls and audit trails.
- Data Warehouse/Lake: For analytical purposes, feeding into reporting and fraud analytics, often using technologies like Snowflake, BigQuery, or a Hadoop ecosystem.
- Asynchronous Messaging & Eventing:
Crucial for decoupling services and handling variable load.- Message Brokers (e.g., Kafka, RabbitMQ, Google Pub/Sub):Used extensively for decoupling services, handling peak loads, implementing event sourcing (e.g., transaction status changes as events), and ensuring reliable delivery of webhooks. Essential for maintaining responsiveness under heavy load.
- Task Queues (e.g., Celery with Redis/RabbitMQ): For background jobs like settlement file generation, large report generation, or asynchronous refunds that do not require immediate responses.
- Monitoring, Logging & Alerting:
The eyes and ears of the operational team.- Distributed Tracing (e.g., Jaeger, Zipkin, OpenTelemetry):Essential for understanding latency and pinpointing bottlenecks across microservices in a complex distributed system, tracing a single request’s journey.
- Centralized Logging (e.g., ELK Stack, Splunk, Datadog):Aggregating logs from all services with robust search and analysis capabilities, crucial for incident response, auditing, and compliance.
- Metrics & Dashboards (e.g., Prometheus/Grafana, Datadog):Real-time visibility into system health, API latency, transaction throughput, error rates, and key business metrics.
- Intrusion Detection/Prevention Systems (IDS/IPS): Monitoring network traffic for suspicious activity and proactively blocking threats.
4. The Critical Path: Transaction Flow Deep Dive
Let’s refine the authorization flow, highlighting specific protocols and challenges, and considering real-world scenarios and potential failures.
- Cardholder Input: A cardholder enters CHD on a merchant’s payment form. To minimize the merchant’s PCI scope (often achieving SAQ A-EP), the merchant typically uses a gateway-provided JavaScript SDK (e.g., hosted fields within an iframe). This SDK encrypts the data client-side before it leaves the browser.
- Encrypted Data Transmission & Tokenization: The encrypted CHD is sent directly from the client browser via TLS to the gateway’s secure Tokenization Service. The Tokenization Service, protected by Hardware Security Modules (HSMs), decrypts the CHD, generates a unique, non-sensitive token (e.g., a UUID or a format-preserving token), securely stores the token-to-PAN mapping in the Token Vault, and returns the token to the client.
- Merchant Authorization Request: The merchant’s backend server, now holding only the token (never the actual CHD), sends an authorization request to the gateway’s API Gateway. This request includes the token, transaction amount, currency, merchant ID, and any relevant order details.
- Gateway Core Processing:
- API Gateway: Authenticates the merchant (e.g., API key validation), performs basic request validation, applies rate limits, and routes the request to the TransactionProcessingEngine.
- Idempotency Check: The TransactionProcessingEngine first checks for idempotency using a unique requestId provided by the merchant to prevent duplicate processing if the request is retried.
- Fraud Evaluation: The RiskManagementService consumes the transaction details. It might perform lookups against velocity checks, blocklists, and execute ML inference models to generate a real-time risk score. Based on this, it might trigger 3D Secure 2.x authentication via an integration with a Directory Server (DS) or immediately decline the transaction.
- Dynamic Routing: The RoutingService analyzes the transaction (e.g., BIN lookup to determine card type/issuer, merchant’s preferred processors, real-time processor performance metrics) to select the optimal NetworkAdapterService.
- Real Scenario (High Volume Scaling): Handling 10,000 transactions per second (TPS) during a flash sale requires this routing to be near-instantaneous. The routing logic must be highly optimized, potentially residing in-memory or a low-latency distributed cache, to avoid adding significant latency to each transaction. Concurrency mechanisms like non-blocking I/O and reactive programming paradigms are crucial here.
- Network Adapter (Protocol Translation): The chosen NetworkAdapterService retrieves the PAN from the Token Vault (under strict access controls and HSM protection), constructs the ISO 8583 Authorization Request (MessageType 0100). It meticulously populates data elements (DEs) such as Primary Account Number (DE 2), Processing Code (DE 3), Amount (DE 4), STAN (System Trace Audit Number – DE 11), Local Transaction Time/Date (DE 12/13), Expiration Date (DE 14), Merchant Type (DE 18), POS Entry Mode (DE 22), etc. It then establishes a secure connection (often dedicated leased lines or VPN over MPLS, secured by strong cryptography) to the acquiring processor.
- Failure Case (Acquirer Outage): If an acquiring processor becomes unresponsive (e.g., network timeout, API errors), the NetworkAdapterService (or the RoutingServiceupstream) must rapidly detect this via active health checks and automatically failover to a secondary, pre-configured acquirer without manual intervention. This requires pre-negotiated contracts with multiple acquirers and robust retry logic with exponential backoff on the gateway side.
- Acquiring Bank to Payment Network: The acquiring processor receives the ISO 8583 message, performs its own validation, and forwards it to the relevant card scheme (e.g., VisaNet, Mastercard IPS).
- Payment Network to Issuing Bank: The card scheme routes the request to the correct Issuing Bank based on the BIN.
- Issuing Bank Decision: The issuing bank performs its own risk assessments, validates the cardholder’s account for funds/credit, and decides to approve or decline. It sends back an ISO 8583 Authorization Response (MessageType 0110) with an Authorization Code (DE 38) for approvals or a Response Code (DE 39) for declines.
- Response Back to Gateway: The response traverses back through the payment network, the acquiring bank, and finally to the gateway’s NetworkAdapterService.
- Gateway Final Processing:
- The NetworkAdapterService parses the ISO 8583 response.
- The TransactionProcessingEngine updates the transaction status in its database, logs all details for auditing, and performs any post-authorization fraud checks.
- The gateway responds synchronously to the merchant’s API call.
- An asynchronous WebhookService might push notifications to the merchant for eventual consistency or specific events (e.g., payment status change, chargeback).
- Failure Case (Webhook Delivery Failure): If a merchant’s webhook endpoint is down or unresponsive, the WebhookService must implement a robust retry mechanism (e.g., exponential backoff) with a defined maximum number of retries. Persistent failures should be moved to a Dead Letter Queue (DLQ) for manual inspection and potential re-processing, preventing data loss or out-of-sync states.
- Latency Scenario (Authorization Timeout): If the round-trip time for an authorization exceeds a predefined threshold (e.g., >500ms), the gateway might implement a “soft timeout.” It could respond to the merchant with a “pending” status while continuing to wait for the issuing bank’s response. This requires careful state management and robust reconciliation processes to avoid orphan transactions.
Settlement: This is a batch process distinct from authorization. Typically, at predefined intervals (e.g., end of day, multiple times a day), the gateway generates a batch of authorized (and captured) transactions. This batch is formatted into a Financial Transaction Advice (ISO 8583 Message Type 0120/0121) or a proprietary file format (e.g., an SFTP file with fixed-width records) and sent to the acquiring bank for clearing and settlement. This triggers the actual movement of funds from the issuing bank to the acquiring bank and ultimately to the merchant’s account. The gateway must rigorously reconcile these submitted batches with the actual settlement reports received from the acquiring bank.
* Failure Case (Settlement File Rejection): If a settlement file is rejected by the acquirer due to formatting errors, missing data, or inconsistencies, the gateway must have automated alerts, robust logging to identify the root cause, and mechanisms to regenerate and resubmit the corrected file. This often involves manual review by an operations team due to the financial criticality.
5. Engineering Considerations: Building for Scale, Security, and Reliability (Deep Dive)
- PCI DSS Compliance (Beyond Basics):
- Scope Reduction: Architecting with P2PE solutions or hosted fields (SAQ A) is ideal to minimize the merchant’s PCI burden. The gateway itself must achieve PCI DSS Level 1 Service Provider certification, involving annual QSA (Qualified Security Assessor) audits and quarterly network scans.
- Separation of Duties: Strict role-based access control (RBAC) and segregation of duties (SoD) are imperative for all personnel accessing CHD environments.
- Vulnerability Management: Continuous scanning (e.g., Nessus, Qualys) and regular penetration testing by independent third parties are non-negotiable.
- File Integrity Monitoring (FIM): For critical system files and CHD data stores, alerting on any unauthorized changes.
- High Availability & Disaster Recovery (Mission Critical):
- Multi-Region Deployment: Active-active deployments across geographically diverse regions for maximum resilience against regional outages. This necessitates sophisticated data synchronization strategies (e.g., cross-region database replication, event sourcing).
- Chaos Engineering: Proactively inject failures (e.g., using tools like Gremlin or Netflix’s Chaos Monkey) to test resilience, identify weak points in the system, and validate failover mechanisms.
- RTO/RPO: Defining and achieving aggressive Recovery Time Objectives (RTO) and Recovery Point Objectives (RPO) for different service tiers, often aiming for near-zero RTO/RPO for core transaction processing.
- Scalability (Handling Bursts):
- Cloud-Native & Serverless: Leveraging managed services (e.g., AWS Lambda, Fargate, Google Cloud Run) for stateless components, abstracting infrastructure scaling, and enabling auto-scaling capabilities.
- Distributed Caching: Using in-memory data stores like Redis Cluster or Memcached for session data, token lookups (with appropriate TTLs and invalidation strategies), and rate limiting counters.
- Connection Pooling: Efficiently managing persistent connections to external systems (acquiring banks, databases) to reduce overhead, particularly for protocols like ISO 8583 which often use long-lived connections.
- Backpressure Handling: Designing systems to gracefully handle overload (e.g., using circuit breakers, bulkheads, adaptive concurrency limits, and intelligent queuing) to prevent cascading failures throughout the system.
- Security Best Practices (Threat Modeling & Proactive Defenses):
- Threat Modeling (e.g., STRIDE): Systematically identify potential threats and vulnerabilities at each stage of the transaction flow during the design phase.
- Zero Trust Architecture: Assume no internal network is safe; implement micro-segmentation and strong authentication for all inter-service communication using mutual TLS (mTLS).
- Code Review & Secure Development Lifecycle (SDLC):Integrating security checks (SAST/DAST tools, manual security reviews) into every phase of development.
- Ephemeral Environments: Use immutable infrastructure and regularly refresh servers/containers to minimize configuration drift and potential persistent threats.
- Secure API Design: Using cryptographic signatures for requests, mutual TLS (mTLS) for internal service-to-service communication, and robust input sanitization.
- Latency & Performance (Real-time Demands):
- Network Optimization: Utilizing private interconnects (e.g., AWS Direct Connect, Azure ExpressRoute) for low-latency, high-throughput connections to financial partners.
- Database Tuning: Indexing, query optimization, connection pooling, and choosing the right database for the workload (e.g., columnar for analytics, row-oriented for transactional).
- Code Optimization: Profile and optimize critical paths for CPU and memory usage using tools like profilers.
- Event-Driven Microservices: Decoupling synchronous paths from asynchronous processes to ensure core transaction flow is not blocked.
- Observability (Operational Excellence):
- Service Mesh (e.g., Istio, Linkerd): Provides traffic management, security, and observability features at the platform layer for microservices, simplifying mTLS, tracing, and metrics collection.
- Business Transaction Monitoring (BTM): Tracking key business metrics and converting them into actionable alerts (e.g., authorization success rate drops, average transaction value changes).
- Synthetic Monitoring: Proactively testing critical transaction paths from external locations to catch issues before real users are impacted.
- Error Handling & Compensation (Saga, Circuit Breakers):
- Saga Pattern: For long-running, distributed transactions (e.g., a capture that fails after authorization), use a Saga pattern (orchestration or choreography) to ensure atomicity and consistency, with compensating transactions for failures.
- Circuit Breakers: Implement circuit breakers (e.g., Resilience4j, Hystrix) to prevent cascading failures when external dependencies (like an acquirer API) become unavailable or slow.
- Dead Letter Queues (DLQs): For messages that cannot be processed successfully, move them to a DLQ for later analysis and reprocessing.
- Regulatory & Global Considerations:
- PSD2 & SCA: Implement support for EMV 3-D Secure 2.x, which allows for risk-based authentication and “frictionless flows” (where the issuer can approve without explicit cardholder interaction). This is a complex integration involving message flows between the Merchant, Gateway, Directory Server (DS), and Access Control Server (ACS). Refer to the EMV 3-D Secure Protocol and Core Functions Specification for comprehensive details.
- Data Residency: Ensuring customer data (especially CHD and personal data) is stored and processed within specific geographic boundaries as required by local laws (e.g., GDPR, local payment schemes).
5.1. Business and Operational Dimensions
Beyond the pure engineering aspects, a successful payment gateway operates within a complex financial and regulatory landscape. Architects and engineers must understand these dimensions to design truly robust and viable solutions.
- Banking and Acquirer Relationships: Establishing and maintaining robust relationships with multiple acquiring banks and processors is crucial for routing flexibility, redundancy, and cost optimization. This involves legal agreements, complex API integration negotiations, and ongoing operational liaison for issues and changes.
- KYC/AML Workflows: Robust Know Your Customer (KYC) and Anti-Money Laundering (AML) processes are non-negotiable for merchant onboarding and ongoing transaction monitoring. This necessitates integrating with third-party identity verification services and adherence to global financial regulations (e.g., FinCEN guidelines in the US, FATF recommendations globally).
- Dispute and Chargeback Management: This represents a significant operational overhead. The gateway needs specialized systems to automatically track chargebacks, manage evidence submission for disputes (often within strict timeframes), and reconcile outcomes. Automated tools can significantly reduce the manual burden and improve success rates in reversing chargebacks.
- Service Level Agreements (SLAs) Monitoring: Critical for both internal operations and merchant satisfaction. SLAs define expected uptime, transaction latency, and authorization success rates. Continuous, real-time monitoring of these metrics and proactive alerting are essential for meeting contractual commitments and maintaining trust.
- Fee Management & Payouts: The gateway handles complex fee calculations that include interchange fees (paid to the issuing bank), scheme fees (paid to card networks), processing fees (by acquirers), and its own gateway fees. It also manages the intricate payout schedules to merchants. This requires a robust, audited financial reconciliation engine to ensure accuracy.
6. Reference Architecture & Example Technology Stack
A well-designed payment gateway architecture must balance scalability, security, and fault tolerance while ensuring compliance with stringent financial and regulatory standards. The diagram below illustrates a reference architecture that brings together these priorities through modular microservices, distributed persistence layers, and real-time data orchestration.
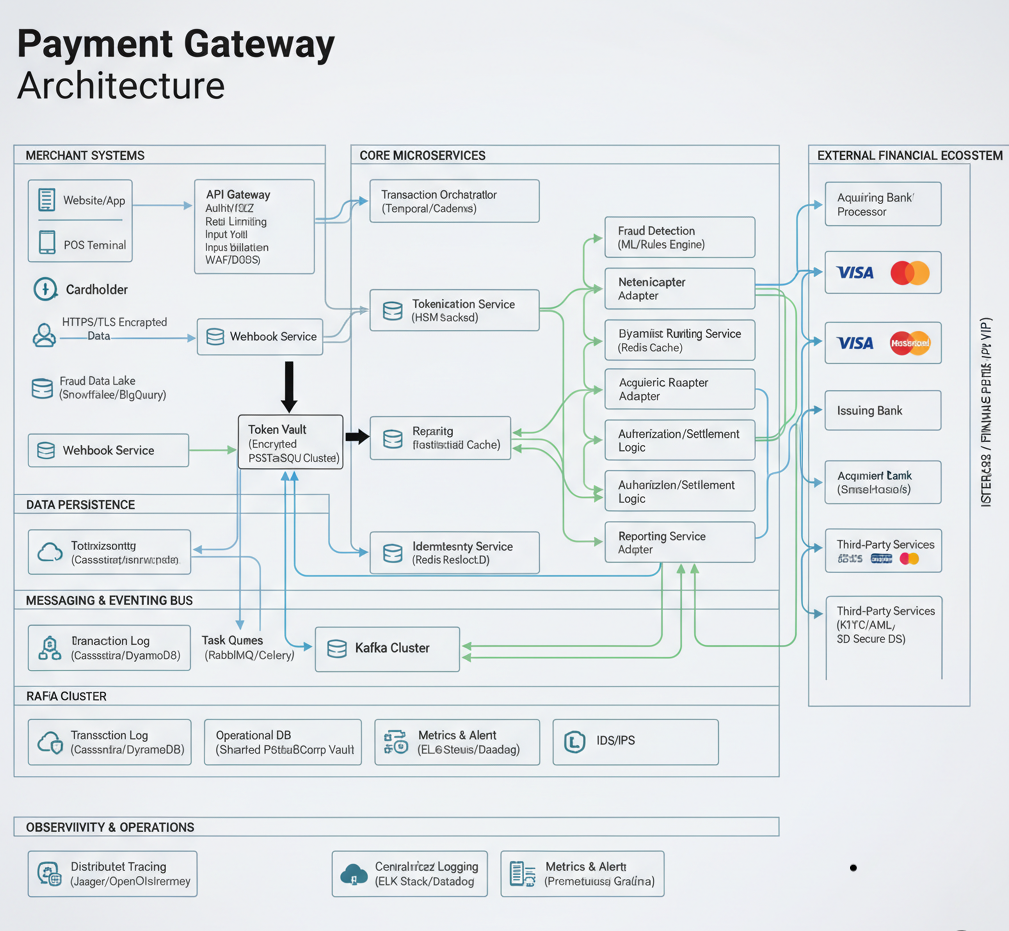
Below is a detailed breakdown of each major component represented in the diagram.
Merchant Systems Layer
Merchant Interfaces (Website/App, POS Terminal):
These represent the merchant’s front-end systems where transactions originate. All sensitive cardholder interactions occur here, secured by HTTPS/TLS encryption and client-side tokenization SDKs to minimize PCI scope.
API Gateway:
Acts as the primary ingress point for merchant applications. Equipped with authentication (JWT/OAuth2), rate limiting, input validation, and WAF/DDoS protection, this ensures secure and reliable access control. It exposes REST/GraphQL endpoints for authorization, capture, refund, and reconciliation requests.
Webhook Service:
Responsible for asynchronous event notifications—such as payment status updates or settlement completions—back to merchants. It implements retry mechanisms, DLQs (Dead Letter Queues), and exponential backoff strategies for guaranteed delivery.
Fraud Data Lake:
Centralized repository (e.g., Snowflake or BigQuery) for aggregating transaction history, behavioral data, and external threat feeds. It supports machine learning models and analytics for fraud prevention and performance optimization.
Core Microservice Layer
At the heart of the architecture lies a collection of loosely coupled microservices, each responsible for a single domain of functionality. These communicate via Kafka or gRPC, ensuring resilience, scalability, and observability.
Transaction Orchestrator
Implements workflow management using Temporal or Cadence, coordinating end-to-end transaction lifecycles—from authorization to settlement and refund. It ensures idempotency, retries, and compensation logic for distributed transactions (Saga pattern).
Tokenization Service
Secures CHD (Cardholder Data) using Hardware Security Modules (HSMs) for encryption and format-preserving tokenization. Tokens are stored in a dedicated Token Vault (PCI DSS Level 1 compliant), isolating sensitive data from all other systems.
Repairing Service
Provides real-time reconciliation and correction of transient errors or delayed transaction updates. Often implemented as a statistical cache to detect anomalies in authorization/settlement flows.
Identity Service
Maintains unique merchant and user identities, leveraging Redis or Resilient Distributed Cache (RDC) for low-latency lookups. Supports authentication, authorization, and KYC integrations.
Fraud Detection Service
Built around a Machine Learning and Rules Engine, it combines behavioral analytics, transaction velocity checks, and device fingerprinting to generate real-time fraud scores. Integration with consortium data and third-party AML services enhances risk profiling.
Dynamic Routing Service
Implements intelligent acquirer selection logic using parameters like BIN, currency, transaction value, and acquirer health. Leveraging Redis caching for near-instant routing decisions ensures minimal latency even under high TPS (Transactions Per Second) conditions.
Acquirer and Network Adapters
Adapters (e.g., NetCenAdapter, AcquirerAdapter) normalize communication across heterogeneous financial systems—whether ISO 8583 or proprietary APIs. They manage connection pooling, message translation, and failover between multiple acquirers.
Authorization and Settlement Logic
This dual-layer component governs transaction approval, capture, refund, and settlement cycles. It supports eventual consistency, transactional guarantees, and asynchronous settlement batching aligned with acquirer cut-off times.
Reporting Service
Aggregates transaction data, generates reconciliation files, and exposes financial reporting APIs. It also feeds data into analytical dashboards for merchants and internal finance teams.
Data Persistence Layer
Transaction Log:
A high-throughput immutable log (e.g., Cassandra or DynamoDB) storing every transaction event for auditability and compliance.
Operational Databases:
Shared relational databases (e.g., PostgreSQL or MySQL) that maintain merchant configurations, metadata, and API credentials.
Token Vault:
Encrypted data cluster dedicated solely to storing token-to-PAN mappings. Access is strictly controlled via HSM-integrated KMS policies and full audit trails.
Identity Store:
Implements merchant and user authentication/authorization records, leveraging Redis for real-time identity checks.
Messaging & Event Bus
Kafka Cluster:
Serves as the backbone for asynchronous communication, event sourcing, and real-time processing pipelines. Enables scalable event-driven microservices and replayable transaction events.
Task Queues (RabbitMQ, Celery):
Used for deferred and background tasks—such as settlement file generation, webhook retries, or periodic reconciliation processes. Offers fault-tolerant and distributed execution models.
Observability & Operations
Distributed Tracing:
Tools like Jaeger or OpenTelemetry provide end-to-end visibility across microservice calls, essential for debugging latency issues and understanding transaction flow paths.
Centralized Logging:
ELK Stack (Elasticsearch, Logstash, Kibana) or Datadog aggregates logs from all services into searchable dashboards for operational and compliance monitoring.
Metrics & Alerts:
Systems like Prometheus and Grafana monitor key KPIs—TPS, latency, error rates, fraud detection performance—and trigger alerts for anomalies. Coupled with ELO Stack/Datadog, they form the operational nerve center.
Intrusion Detection/Prevention (IDS/IPS):
Monitors traffic patterns, detects potential intrusions, and automatically mitigates attacks in real time—reinforcing Zero Trust principles across network layers.
External Financial Ecosystem
Acquiring Banks & Processors:
Partners that facilitate merchant settlements and handle the actual flow of funds. The gateway maintains persistent secure channels to these entities.
Card Networks (Visa, Mastercard):
Global networks governing transaction standards (ISO 8583), risk management, and interchange settlements. The gateway connects via certified, encrypted connections to their endpoints.
Issuing Banks:
Institutions authorizing or declining transactions based on cardholder credit/funds. Integrations often require strict compliance and round-trip latency guarantees (<500ms).
Third-Party Services (AML/KYC, Fraud, 3D Secure):
External integrations that provide additional compliance, fraud intelligence, and authentication layers. These include services for AML screening, KYC verification, and EMV 3D Secure (SCA compliance).
Tech Stack
| Component | Example Technologies |
|---|---|
| API Gateway & Edge | Kong, NGINX, AWS API Gateway, Envoy |
| Workflow Engine | Temporal, Cadence |
| Microservices | Python (FastAPI), Go, Java (Spring Boot), Node.js |
| Databases | PostgreSQL, Cassandra, Redis, DynamoDB |
| Message Broker | Kafka, RabbitMQ |
| HSM & KMS | Thales HSM, AWS CloudHSM, HashiCorp Vault |
| Monitoring & Logging | Prometheus, Grafana, ELK Stack, Datadog |
| Fraud & ML Pipelines | Kafka Streams, Flink, TensorFlow, XGBoost |
| CI/CD & Infrastructure | Jenkins, ArgoCD, Terraform, Kubernetes |
| Security & Compliance | PCI DSS L1, mTLS, OAuth2, Zero Trust Architecture |
7. Future Trends $ Evolution
The payment gateway domain is undergoing rapid transformation driven by technological innovation, regulatory changes, and evolving customer expectations. Below are the trends shaping the next generation of gateway architectures:
- Composable Finance & Open APIs: Modular, API-driven financial systems allowing seamless integration with new fintech services and alternative payment methods (APMs).
- Real-Time Payments (RTP): The move toward 24×7 instant settlements, powered by open banking and ISO 20022 adoption.
- AI-Driven Fraud Detection: Next-gen fraud engines leveraging graph neural networks (GNNs) and federated learning for collective fraud intelligence.
- Decentralized Payments & Blockchain: Secure, auditable, and programmable payment flows using smart contracts and tokenized assets.
- Quantum-Resistant Cryptography: Preparing for post-quantum encryption standards to future-proof sensitive data protection.
- Serverless & Edge Payments: Reducing latency by executing payment logic closer to end-users via edge computing and function-as-a-service models.
- Sustainability & Green Payments: Optimization of energy usage and adoption of carbon-efficient infrastructure in payment data centers.
Conclusion
Building a payment gateway isn’t merely about enabling transactions—it’s about engineering trust, scalability, and compliance at global scale. From tokenization and orchestration to fraud prevention and observability, each layer is a mission-critical piece in ensuring security, speed, and reliability.
The architecture we explored embodies the convergence of distributed systems engineering, financial compliance, and cloud-native resilience. As digital commerce continues to evolve, gateways that embrace AI, real-time processing, and zero-trust security will define the future of seamless, intelligent, and secure payments.
